An overview of the process and components of a risk assessment for high-security facilities
The risk management process is not unique to SCIFs or SAPFs, but it’s key for getting your facility accredited. The assessment will look different for each different project you may work on. Every location comes with its unique threats and vulnerabilities that you’ll need to plan for. Here’s a breakdown of the process and its components to help you get started.

What is the Risk Management Process?
SCIF risk management is an assessment performed to find possible vulnerabilities and threats to your facility. Once those are known, you evaluate the probability of something going wrong and the consequences if they do.
This process is used to decide where your facility needs security mitigations, augmentations, or even reductions. You record the results of the assessment in your project’s Construction Security Plan (CSP).
Different government elements have different ways of measuring risk. Many will try to quantify the risk, assigning values to threats in order to scale what mitigations are necessary. Others may take a less quantifiable approach.
Several security professionals use the National Institute of Standards and Technology (NIST) Risk Management Framework (RMF), which is typically used for network architecture and security, as a framework for performing their risk assessment.
Starting SCIF Risk Management
Your Accrediting Official (AO) is a key player in the risk management process and is ultimately responsible for the final assessment and facility accreditation. They’ll work in collaboration with the Site Security Manager (SSM) to complete the assessment. Your SSM will be able to provide more of an internal overview of your project; the AO will have a more external view of factors such as locally known threats, especially if they have done projects in the area previously.
Unfortunately, AOs have a large case load and can take a while to respond, which can extend your assessment timeline. To help speed things along, a member of the Physical and Technical Security Expert Working Group (PTSWEG) recommended to us that when you start a SCIF project, do your own risk assessment and send your findings to your AO. Sending your own information first saves them time and gives them a starting point, and then they can give further guidance.
The process can take anywhere from two months to six months or more. This depends on the availability of your AO and the amount of information you initially supply them. If you don’t give them anything to start, you’re likely looking at a longer process, as the AO will have to reach back out with questions. Remember, the more you give to your AO up front, the faster they’ll be able to move the process along. This assessment informs the requirements in the design, so you need it done before the AO can sign off on your design plans.
The ICD 705 Tech Spec says that the TEMPEST assessment ideally happens close to the same time and is therefore part of your risk assessment phase. This won’t always be the case. The AO may include TEMPEST mitigations in their risk assessment, but a Certified TEMPEST Technical Authority (CTTA) evaluation can take place later in your project timeline, even during construction.
Factors of Risk Management
SCIF risk management contains four components: threat analysis, vulnerability analysis, probability analysis and consequence analysis. Each will factor into which mitigations your facility will need.
Threat Analysis
As part of your threat analysis, you evaluate anything that could potentially cause harm to your facility. This could be a local known bad actor who would attack the facility, a negligent insider threat, or a possible cyber-attack. You’ll also have to assume that every vendor who works on your project is capable of posing a threat due to the information they possess.
These threats could harm your facility by intrusion, destruction or disclosure. They can come from outside your project, but tradesmen you hire and people within your company can also present a potential threat.
Vulnerability Analysis
Vulnerabilities are places where your facility could be weak to attack. The process will evaluate any vulnerabilities your project may have that could be exploited. For example, if your SCIF is in a leased building shared with other tenants, that could be a weak point for your facility.
For this analysis, you’re looking for any weaknesses that bad actors could take advantage of in order to breach your SCIF or get information about the work taking place in your facility.
Probability Analysis
Once you know what your threats and vulnerabilities are, you must determine how likely they are to cause an issue. If your facility shares its building with other tenants, there may be some risk of them trying to breach your facility or data. In a place like Washington, D.C., where there are a lot of foreign embassies, you may see a higher probability of an attack.
Consequence Analysis
If something does go wrong, the consequence analysis will evaluate how much damage it would do to your facility, organization, or the information you process. If your workers rely on a bridge to get to work, and that bridge is closed one day, what will be the consequences if your workers are late as a result of traffic? For some projects, this may be minimal, but for a facility doing a critical 24/7 process, you may have more serious repercussions.
If your facility is breached, there may be minor consequences, but there is no such thing as no consequences in that situation. For example, if someone breaches a space in your facility that is discussion only, they may not have the ability to steal classified information, but they could leave behind a listening device that allows them to gather it later on.
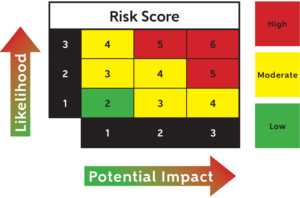
An example of how an AO might quantify risk
Once you’ve gone through the SCIF risk management process and have this information, you’re able to figure out what mitigations will be critical to your facility and where you may be able to ease up. This will be a main driver of cost, since it will tell you what you need in the way of physical hardening, acoustic protections, or other mitigations.
The risk assessment process is one of the most important things in getting your SCIF built right, so it’s crucial to get it done right. At Adamo, our experts can partner with your team to guide you through the process and ensure your assessment goes smoothly.




