Insider threat is the most persistent and prevalent type of security threat in the country. This type of threat occurs when an insider (an employee or contractor with authorized access) wittingly or unwittingly misuses their authorized access to negatively harm a company or organization.
The risk of insider threat is high for any company or organization, governmental and non-governmental alike. If encountered, sensitive information could be exposed, sabotage and fraud could occur, employee and customer data could be stolen and more, resulting in high costs to repair the damage. In fact, it is estimated that the average annual cost for each organization that experiences insider threat is $15.4 million. That is why it’s so critical for businesses to develop an Insider Threat Program to prevent the threats before they happen or detect them early to minimize damage to your organization.
Types of Insider Threat
There are three types of insider threats we will highlight: witting, unwitting and foreign intelligence agencies/officers. Many say that witting threats are often motivated by ego, money or allegiance to an ideology. One classic example of witting insider threat is Edward Snowden’s leak of highly classified information from the National Security Agency (NSA) while a trusted contract employee. Another, and possibly the chief example, is Robert Hanssen, who spied for Soviet and Russian intelligence services for over 20 years during his career as an FBI agent. Both of these men had security clearances but abused their authority and wittingly compromised national security.
While many believe insider threats are all malicious, the numerous unwitting threats are often caused by pure negligence. These negligent errors account for 56% of insider threats and cost organizations approximately $484,931 per incident.* Many examples of this type of threat can be found in the success of phishing emails. The careless act of opening emails from unknown sources or clicking on web links before thinking can result in compromising a company’s entire database and secure information.
A well-known example of the third type of insider threat, foreign intelligence, was Greg Chung acting as an agent for the People’s Republic of China. Chung held a security clearance while working in the U.S. at Rockwell International, later Boeing, in the Space Shuttle program. For nearly 30 years, he gathered and shared restricted technology and trade secrets with China, endangering U.S. national security.
How to Prevent and Detect
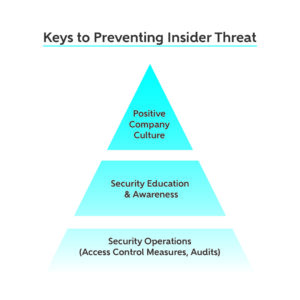
The best way to prevent and detect an insider threat is to establish an Insider Threat Program that utilizes a combination of:
- Security operations
- Security education
- A company culture of trust and care
In order to maintain a facility clearance (FCL), the first two are required components of an Insider Threat Program, as mandated by the National Industrial Security Program (NISPOM), but all three are recommended and successful in detecting and preventing an insider threat.
A key element for security operations is access control including these two principles: Least Access (giving staff the least amount of access needed to get their job done) and Need to Know (giving staff only the information they need to know and no more). These principles can lessen the amount of insider threat damage and help identify those employees who could potentially be a threat to security if found to be reaching beyond their access.
In addition to operations, security education is vital for the staff in a company or organization to know what to look for as signs of threats or areas of vulnerability. Also helpful is knowing how to identify counterproductive work behaviors, such as coming into the office at odd times, a drastic mood change in an employee or a drop in work performance. These behaviors can be significant indicators of insider threats or potential threats.
When these behaviors are identified, they should be discussed, documented and reported to an established insider threat working group. This group should be composed of key personnel and internal stakeholders such as human resources, program managers, directors, IT, employee relations and so on. The group will help create a conduit for communication and bubble up indicators for different avenues of security. At its best, the working group should use these indicators to help those employees suspected as possible threats get back on track. The group should also lead the charge for education and monitoring access controls.
When a company culture of trust and care is established, then an organization is automatically setting its sights on one another, which will help prevent someone displaying insider threats from going undetected. This culture is cultivated by management and peers taking a genuine interest in each other while understanding threat signs, which will then make an insider threat more likely to be spotted and provide a path for that insider to be turned back into a productive worker.
Even if an insider threat goes undetected, having good controls and programs in place can still limit the damage. The more established proper procedures are, the more quickly threats can be mitigated. The quicker a threat is detected and addressed, the less costly it will be for an organization.*
Your Insider Threat Program
NISPOM requires government contractors to appoint a Facility Security Officer (FSO) as well as an Insider Threat Program Senior Official (ITPSO) to establish an insider threat program that will detect, deter and mitigate insider threats (see Procedures in 32 CFR Part 117.7). This program requires numerous procedures and protocols to be followed to maintain an FCL, including creating an insider threat working group and more.
If you and your organization need support for your FSO or are looking to initiate and enhance your Insider Threat Program, Adamo can help. Here you can find details for our FSO support, including Insider Threat Program creation and management. Contact us to learn more!




