How can you improve document control of classified information? If your company holds a Facility Clearance (FCL), good document control is a key part of maintaining your clearance and preserving national security. The standards for how facilities need to manage their document control can be found in 32 CFR part 117, NISPOM. Responsibility for maintaining good document control falls on the … [Read more...] about Enforcing Good Document Control in Your Cleared Facility
Can Your Smart Security Tech Be Too Smart?
Are we sacrificing security in the name of convenience? As technology becomes more advanced, some of our security systems are able to be controlled without so much as pushing a button. You can remotely engage your system from your phone or shut it off with the sound of your voice. This can save some time, but as we lean more into smart technology, are we putting ourselves into a more vulnerable … [Read more...] about Can Your Smart Security Tech Be Too Smart?
Protecting your PII While Working and Networking
Know what personal information is OK to give away and what to protect When it comes to your Personal Identifiable Information (PII) like your birthdate, address, or driver’s license number, managing what you give out and when is crucial. For those holding a Personnel Clearance (PCL), protecting this information can be even more vital, especially when it comes to sharing information related to … [Read more...] about Protecting your PII While Working and Networking
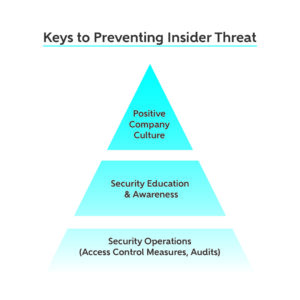
How to Build a Positive Company Culture to Prevent Insider Threat
How you can improve your company culture to stop insider threats before they happen Insider threat incidents in the U.S. have doubled in the last two years, with businesses around the country facing 2,500 internal security breaches daily. Insider threats can cost an organization millions of dollars, but one way to combat these threats is through building a positive company culture. With a … [Read more...] about How to Build a Positive Company Culture to Prevent Insider Threat
Best Practices for Handling Sensitive Information at Home
With COVID-19 numbers still climbing around the country, remote work isn’t going away just yet. Until you return to the office, how you handle your company’s sensitive information—especially in a shared home—is critical. Share these resources and best practices with your security teams to ensure your information stays protected. Security Begins at Home Our newest security awareness poster, … [Read more...] about Best Practices for Handling Sensitive Information at Home
How to Prevent and Detect Insider Threat
Insider threat is the most persistent and prevalent type of security threat in the country. This type of threat occurs when an insider (an employee or contractor with authorized access) wittingly or unwittingly misuses their authorized access to negatively harm a company or organization. The risk of insider threat is high for any company or organization, governmental and non-governmental … [Read more...] about How to Prevent and Detect Insider Threat
How To Be An Effective Security Leader in Uncertain Times
A Message from Adamo’s CEO, Josh Godknecht Hello, security leaders. When I’m talking to security leaders, I’m talking to all of us. Whether your job is professional, vocational security enforcement of some sort, or you’re just a parent, friend or a spouse, a citizen at the grocery store, driving on the freeway, all of us have the responsibility for the well-being of our fellow citizen, our fellow … [Read more...] about How To Be An Effective Security Leader in Uncertain Times