Security in Depth (SID) refers to the multiple layers of security used to safeguard an asset. These security measures function in concentric layers, much like an onion, utilizing a combination of different technologies and security operations to protect against physical threats and forced entries. At their best, these layers should deter, detect, delay and deny unauthorized intrusions.

Just as a castle is protected by multiple layers of protection, so is a facility with security in depth (SID).
Security in Depth Looks Like …
SID can be used in any facility that wants to protect its equipment, materials, documents, data or persons from damage or theft and control movement within the facility. The practice of SID has been around for hundreds of years. Imagine a castle with its moat, drawbridge, outer wall, inner wall, watch towers and so on — all providing layers of security to guard against infiltration, as well as escape with something valuable.
These days, using physical barriers in conjunction with electronic systems and sensors and security ops is a must to maximize SID. These interdependent tactics will aid in deterring or intercepting and neutralizing a threat from getting in and out with an asset. The multiple layers in a good SID plan will also increase the chance to detect and respond to threats quickly.
Today’s SID layers might look a bit different from the days of Sir Lancelot, but the concept is the same. Some examples of today’s layered security measures include:
- Signage
- Barriers
- Lighting
- Video surveillance systems
- Alarms and alarm sensors
- Perimeter entry check points
- Visitor entry areas
- Two-way radios
- Screening equipment
- Locks
- Security personnel
- Doors
- Windows
- Layout and construction of a facility
Security in Depth for SCIFs and SAPFs
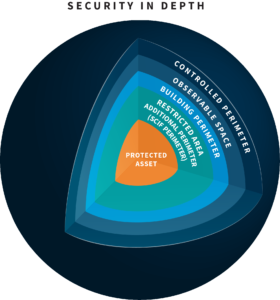
SID for SCIFs (Sensitive Compartmented Information Facilities) and SAPFs (Special Access Program Facilities) is applicable in two ways. First, it begins during the construction of a facility, and second for the operation of that facility once it is established.
During the building phase, a Construction Security Plan (CSP) is utilized to protect the facility and ward against any threats or attacks that might compromise the integrity of the security measures being created, like preventing hidden cameras and listening devices from being planted during construction. Once construction is complete, SID takes on a new form for the operations of the facility.
SID standards, which are defined in the IC Tech Spec for ICD/ICS 705 for SCIFs and SAPFs, are the threshold for quality SID. They can also reduce design costs and eliminate extra security features that would be required if the specifications were not included.
All SCIFs outside the U.S. are required to have SID. Below are the primary acceptable means to achieve SID according to the IC Tech Spec (page 4). At least one of the mitigations is required:
- Military Installations, embassy compounds, U.S. Government Compound or contractor compound with a dedicated response force of U.S. persons.
- Controlled buildings with separate building access controls, alarms, elevator controls, stairwell controls, etc., required to gain access to the buildings or elevators. These controls shall be fully coordinated with a formal agreement or managed by the entity that owns the SCIF.
- Controlled office areas adjacent to or surrounding SCIFs that are protected by alarm equipment installed in accordance with manufacturer’s instructions. These controls shall be fully coordinated with a formal agreement or managed by the entity that owns the SCIF.
- Fenced compounds with access-controlled vehicle gate and/or pedestrian gate.
Defense contractors must demonstrate that their facilities have a competent security approach. They can get a certificate from a Cognizant Security Agency (CSA) that will evaluate the facility and determine if SID has been achieved for accreditation.
To learn more about the specialized standards for your SCIF or SAPF, check out the latest Tech Spec V1.5.
Avoid Security Theater with Security in Depth
Any facility that doesn’t have quality SID really has no security at all. And if you don’t intermingle technology, physical barriers and a process with people’s response, then you are also falling prey to “security theater.” Don’t be left with only the illusion of security; instead, incorporate efficient multilayered security measures to ensure your facility has the proper safeguards to protect your assets.
Lastly, your security team should thoroughly test your facility’s SID. The only way you can truly know if your SID is appropriately working is if you effectively test it.
Adamo is here to help make sure you have sufficient SID to keep your data and assets secure. We offer both educational and technical consulting services to partner with you for your success. Reach out to us today to find out more.




